Instant visibility into underground credential leaks
Search over 75 billion plain text credentials collected from malware logs, combolists, database breaches and dark-web dumps, and get alerted before attackers act.
173B+ records
Millisecond lookup
Real-time alerts
Unlimited searches
API access included
Pay by card or crypto
No hidden fees
Key Features
Built for threat hunters and defenders
Get the fastest, clearest view into malware-harvested leaks.
Plain-text Credentials
Passwords exactly as stolen - no hashes, no redaction.
Email Search
Find every leak containing your email address in one click.
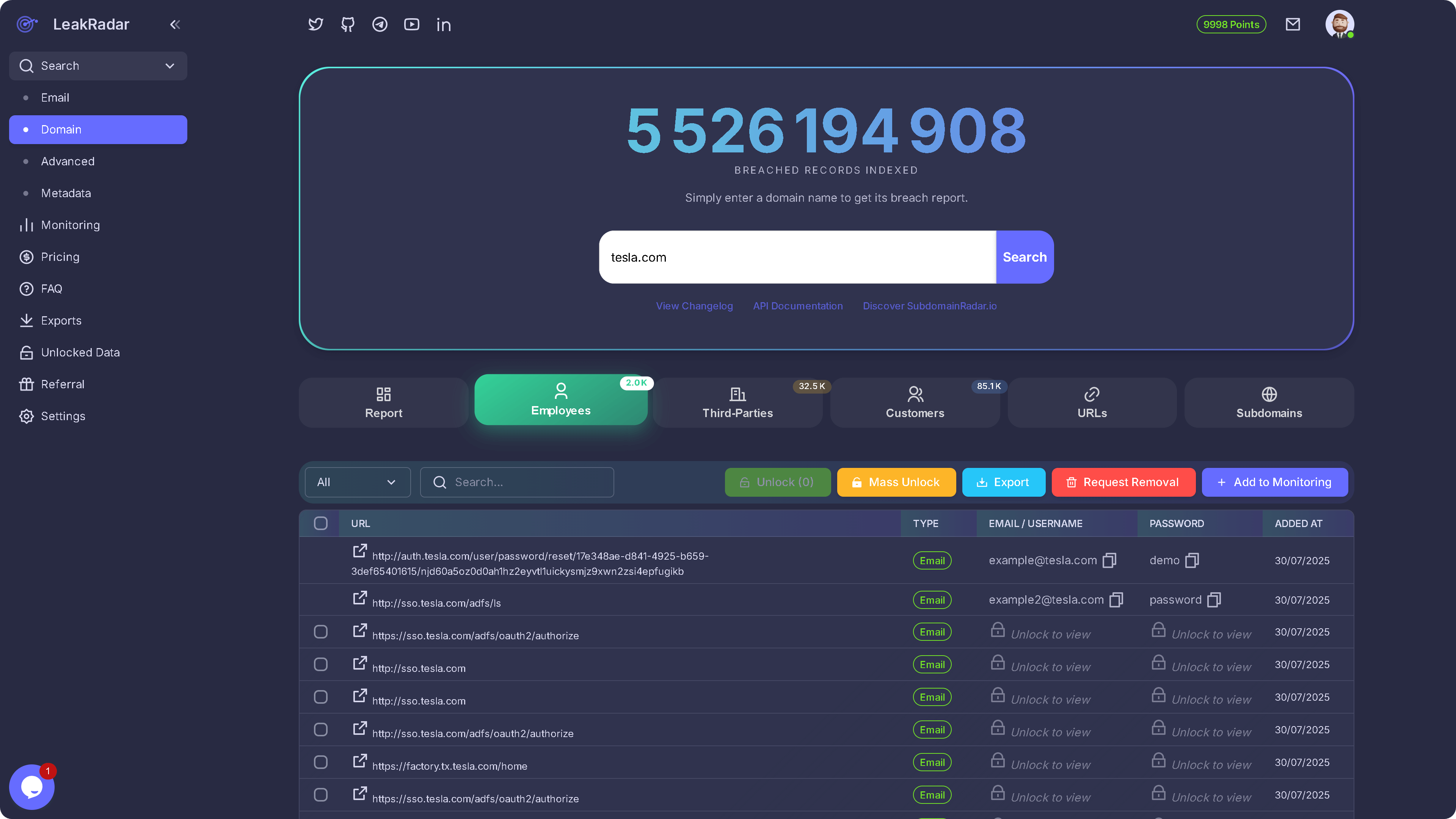
Domain Search
Instantly retrieve every leak where your company domain appears.
Advanced Filters
Search by url, url_host, url_domain, url_tld, username, password, is_email, email_domain, email_host or email_tld.
173B+ Records - Millisecond Lookup
Query over seven billion plain text credentials in a fraction of a second.
API Ready
Integrate LeakRadar into your SOC through a straightforward REST API.
LeakRadar in Action
See how LeakRadar works
Watch our tutorial to learn how to use LeakRadar effectively and get the most out of your subscription.
Pricing Plans
Choose the plan that fits
Instant access, same-day upgrades, cancel anytime.
Unlock equals number of plain-text records you can reveal per day across all searches. Searches are free and unlimited.
We accept all major credit cards and cryptocurrencies.
Cancel anytime, with no fees or questions.
Testimonials
Real stories from our users
Hear how LeakRadar helps secure companies and rewards security researchers.
"Thanks to LeakRadar, we got an instant heads up when some of our team passwords surfaced in an underground leak. We reset them before anyone had the chance to abuse them."
Julie B.
Security Manager - EU fintech"LeakRadar real-time alerts plug straight into our incident-response runbook. Something that used to keep us busy for days now gets fixed in just a couple of hours."
Marc D.
SOC Analyst - MSP, North America"LeakRadar let me slice through leak data, spot the compromised accounts fast, and guide my client through locking them down before the attackers could."
Samira K.
Cybersecurity Consultant - EMEAFAQ
Frequently asked questions
Browse through these FAQs to find answers to commonly asked questions.
Which payment methods do you accept?
Is there a daily data-access limit?
Do you provide an API and can I use it commercially?
For Python developers we also offer an official wrapper: install it with **pip install leakradar** or check the source on GitHub: https://github.com/LeakRadar/leakradar-wrapper.
Rate limits are 30 req/s for all plans, except for Mass Check endpoints (1 req/s) and Advanced Search endpoints (5 req/s).
Where does the data come from?
What does "unlock" a leak mean?
What search types are available and how do they work?
- **Email Search** - Query a single address (e.g. alice@example.com) and instantly see every leak containing it.
- **Domain Search** - Map exposure for a whole domain. Results are automatically categorised into:
- Employees - `email_domain = acme.com AND url_domain = acme.com`
- Third-party accounts - `email_domain = acme.com AND url_domain != acme.com`
- Customers - `url_domain = acme.com AND email_domain != acme.com`
- **Advanced Search** - Combine multiple criteria with boolean operators, wildcards and field filters. You can filter on any of the following fields:
`url, url_host, url_domain, url_tld, url_scheme, url_port, username, password, email_host, email_domain, email_tld`
- **Metadata Search** - Search leaks via information extracted from the HTTP response of each leaked URL. You can match against:
`url, title, meta_description, status_code, body_text`
Do you know when each leak happened?
Ready to try LeakRadar?
Run your first leak search in seconds - no credit card required.
Blog
Latest articles & tutorials
Fresh insights on breach-hunting, malware and threat intel.